CEO Fraud
CEO Fraud, also known as Business Email Compromise (BEC), is a $26 billion worldwide scam according to the FBI. Find out how you can prevent this type of attack and what to do if you become a victim.
What is CEO Fraud?
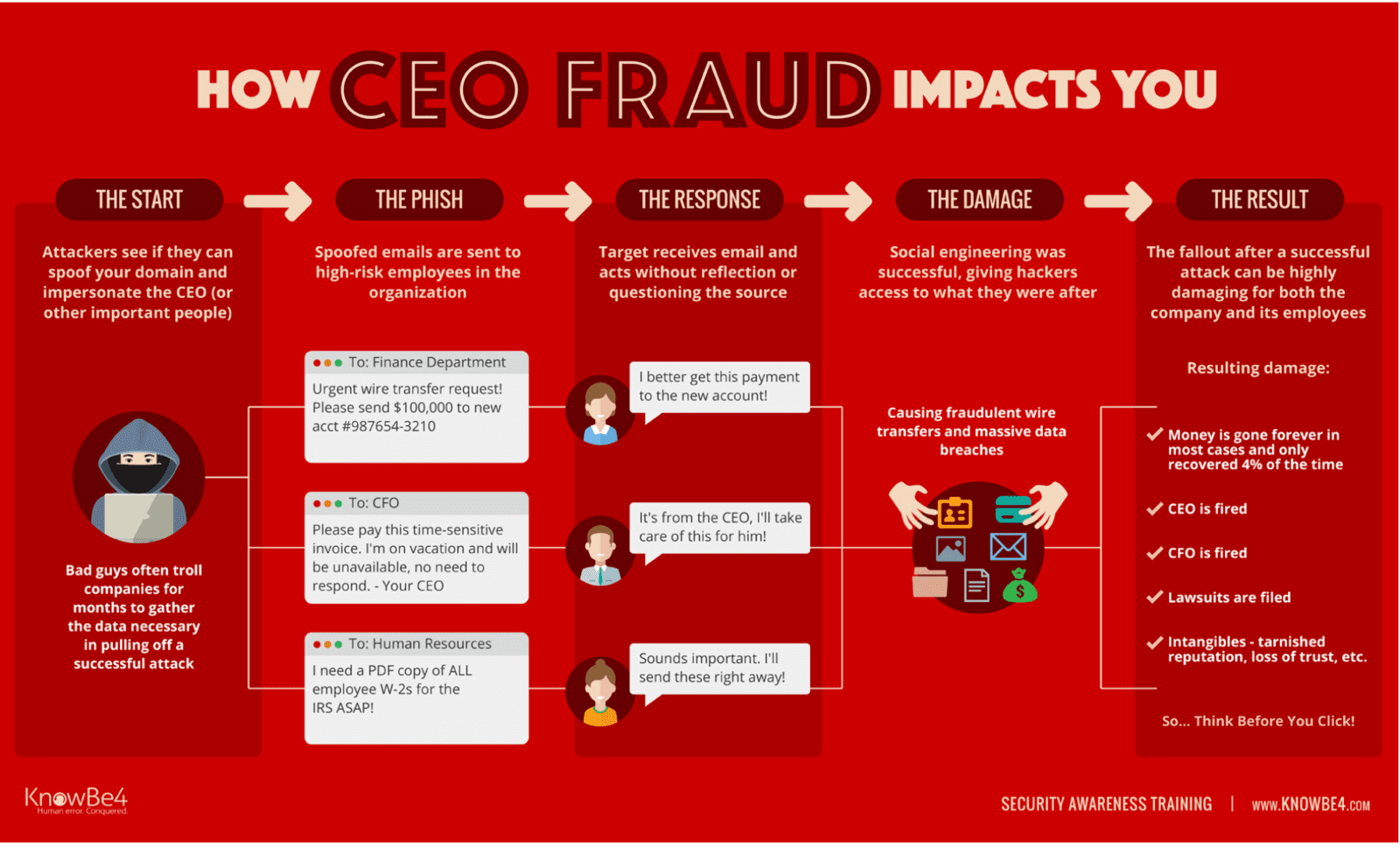
CEO Fraud is a scam in which cyber criminals spoof company email accounts and impersonate executives to try and fool an employee in accounting or HR into executing unauthorised bank transfer, or sending out confidential tax information.
This type of scam is called "Business Email Compromise" and defines BEC is defined as “a sophisticated scam targeting businesses working with foreign suppliers and/or businesses that regularly perform bank payments. The scam is carried out by compromising legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorised transfers of funds.”
According to FBI statistics, CEO fraud is now a $26 billion worldwide scam. Between May 2018 and July 2019, there was a 100% increase in identified global exposed losses. The scam has been reported in 150 countries. Victim complaints filed with financial sources indicate fraudulent transfers have been sent to banks from roughly 140 countries.
Four Attack Vectors
1. Phishing
Phishing emails are sent to large numbers of users simultaneously in an attempt to “fish” sensitive information by posing as reputable sources—often with legitimate-looking logos attached. Banks, credit card providers, delivery firms, law enforcement, and the IRS are a few of the common ones. A phishing campaign typically shoots out emails to huge numbers of users. Most of them are to people who don’t use that bank, for example, but by sheer weight of numbers, these emails arrive at a certain percentage of likely candidates.
2. Spear-Phishing
3. Executive Whaling
Here, the bad guys target top executives and administrators, typically to siphon off money from accounts or steal confidential data. Personalisation and detailed knowledge of the executive and the business are the hallmarks of this type of fraud.
4. Social Engineering
5 Common Scenarios
- Business working with a foreign supplier: This scam takes advantage of a long-standing bank transfer relationship with a supplier, but asks for the funds to be sent to a different account.
- Business receiving or initiating a bank transfer request: By compromising and/or spoofing the email accounts of top executives, another employee receives a message to transfer funds somewhere, or a financial institution receives a request from the company to send funds to another account. These requests appear genuine as they come from the correct email address. The legal sector is targeted in what is called 'Friday Afternoon Fraud' where the criminals try to divert cash transfers from house purchases/sales.
- Business contacts receiving fraudulent correspondence: By taking over an employee’s email account and sending invoices out to company suppliers, money is transferred to bogus accounts.
- Executive and attorney impersonation: The fraudsters pretend to be lawyers or executives dealing with confidential and time-sensitive matters.
- Data theft: Fraudulent emails request either all salary, tax information or a company list of personally identifiable information (PII). These come from compromised and/or spoofed executive email accounts and are sent to the HR department, accounts, auditing departments or anyone who the cyber criminals believe will be helpful.
Who Are The Main Targets?
The label of this category of cyber crime may be CEO fraud, but that doesn’t mean the CEO is always the one in a criminal’s crosshairs. There are at least four other groups of employees considered valuable targets given their roles and access to funds/information:
Finance
The finance department is especially vulnerable in companies that regularly engage in large wire transfers. All too often, sloppy internal policies only demand an email from the CEO or other senior person to initiate the transfer. Cyber criminals usually gain entry via phishing, spend a few months doing recon and formulate a plan. They mirror the usual wire transfer authorisation protocols, hijack a relevant email account and send the request to the appropriate person in finance to transmit the funds. As well as the CFO, this might be anyone in accounts that is authorised to transfer funds.
HR
Executive Team
Every member of the executive team can be considered a high-value target. Many possess some kind of financial authority. If their email accounts are hacked, it generally provides cyber criminals access to all kinds of confidential information, not to mention intelligence on the type of deals that may be ongoing. Thus executive accounts must receive particular attention from a security perspective.
IT
Technology v The Human Firewall
Most efforts towards risk mitigation concentrate on technology. However, these technology safeguards must be supported by what is known as the human firewall. Regardless of how well the defence perimeter is designed the bad guys will always find a way in. They know that employees are the weakest link in any IT system. Thus, cyber criminals continue to rely on phishing and other tricks from the social engineering playbook. The following is a MINIMUM of what to have in place to protect yourself:
- Endpoint Protection
- Email Secure Gateway
- Web Protection
- Firewall
- Two-Factor Authentication
- Fully tried and tested backups!
Take a look at our Security Bundles, or our individual Products, they can be Managed or Unmanaged
- Employees can be the easiest target
- Train and educate your users on cyber threats
- Everyone needs to be able to spot a phishing email
- Regularly test users with phishing email to keep them up to date
- New-school security awareness training is the way to create your own human firewall
Eight Steps To Mitigate Your Risk
Many of the preventative actions go hand-in-hand to create an effective mitigation program


