Spear-Phishing
Spear phishing is a more targeted form of phishing. 91% of successful data breaches start with a spear phishing attack. Get the information you need to defend against this threat.
What is Spear-Phishing?
Spear phishing is an email targeted at a specific individual or department within an organisation that appears to be from a trusted source. It's actually cyber criminals attempting to steal confidential information.
A whopping 91% of cyber attacks and the resulting data breach begin with a spear phishing email, This conclusively shows that users really are the weak link in IT security if they don't receive security awareness training. the weak link in IT security if they don't receive security awareness training.
How It's Done
1. Identify Email Addresses
There are two ways hackers send phishing campaigns: the first is ‘spray-and-pray’ which is a shotgun approach. Get as many email addresses from the organisation they can, and send them all an email that they might click on. The second approach is decide what data you are after, then figure out who has access to that data, and specifically target those people. That is the spear phishing approach, and for instance LinkedIn is extremely useful during this targeting step along with company websites.
There are several ways to get your hands on the email addresses from an organisation. The one favoured by the bad guys is using scripts to harvest email addresses from the large search engines. You’d be surprised how many emails can be captured this way and how big a given organisation's spear phishing attack surface is. Once the bad guys have the email addresses of the few people they are targeting, it's on to step two.
2. Antivirus Evasion
3. Egress Filtering
Hackers can't get the information out of the organisation they are attacking unless the payload sent with the attack allows traffic to exit the organisation. A popular payload is called ‘reverse_https’ because it creates an encrypted tunnel back to the metasploit server, which makes it very hard for security software like intrusion detection or firewalls to detect anything. For those products, exiting phishing data all looks like normal https traffic.
4. Spear Phishing Scenario
5. Sending The Emails
6. Harvesting Treasure
The bad actors don't need to worry about GDPR or fines from the ICO!
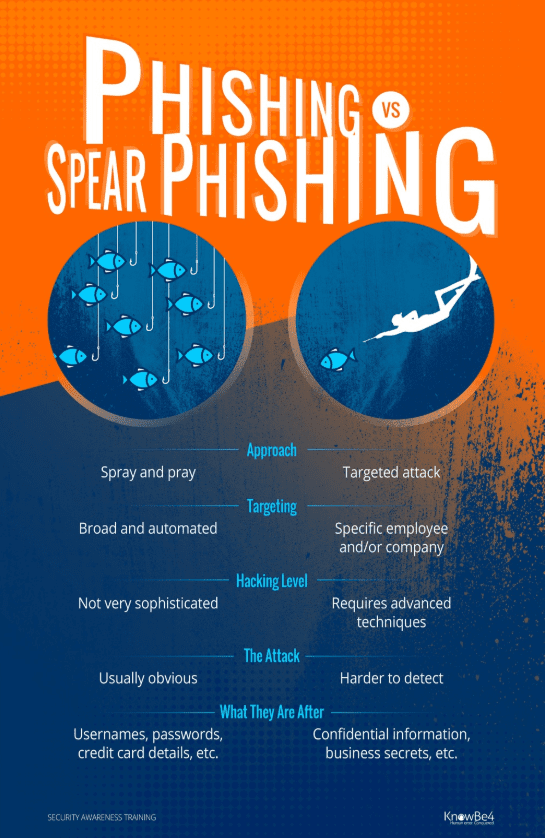
Phishing v Spear-Phishing
While phishing and spear phishing attacks are similar, there are many key differences to be aware of. A phishing campaign is very broad and automated, think 'spray and pray'. It doesn't take a lot of skill to execute a massive phishing campaign. Most phishing attempts are after things like credit card data, usernames and passwords, etc. and are usually a one-and-done attack.
On the other hand, spear phishing is highly targeted, going after a specific employee, company, or individuals within that company. This approach requires advanced hacking techniques and a great amount of research on their targets. Spear phishers are after more valuable data like confidential information, business secrets, and things of that nature. That is why a more targeted approach is required; they find out who has the information they seek and go after that particular person. A spear phishing email is really just the beginning of the attack as the bad guys attempt to get access to the larger network.
Imagine your Marketing Department carrying out an Email Campaign, they will know that the 'spray and pray' method won't be very successful so they will produce a very targeted approach to their campaigns to get maximum ROI, the cyber criminals are following exactly the same process!
Here's an infographic highlighting the differences between phishing and spear phishing.
Preventing Successful Spear-Phishing Attacks
Now, how to mitigate against attacks like this? There is no single approach that will stop this threat, but here is what you need to do to be a hard target for criminals:
- First of all, you need all your defence-in-depth layers in place. Defending against attacks like this is a multi-layer approach. The trick is to make it as hard as possible for the attacker to get through and to not rely on any single security measure to keep your organisation safe.
- Do not have a list of all email addresses of all employees on your website, use a web form instead.
- Regularly scan the Internet for exposed email addresses and/or credentials, you would not be the first one to find one of your user’s username and password on a crime or porn site.
- Never send out sensitive personal information via email. Be wary if you get an email asking you for this info and when in doubt, go directly to the source.
- Enlighten your users about the dangers of oversharing their personal information on social media sites. The more the bad guys know, the more convincing they can be when crafting spear phishing emails.
- Users are your last line of defense! They need to be trained using new-school security awareness training and receive frequent simulated phishing emails to keep them on their toes with security top of mind. We provide the world's largest content library of security awareness training combined with best in class pre- and post simulated phishing testing. Since 91% of successful attacks use spear phishing to get in, this will get you by far the highest ROI for your security budget, with visible proof the training works!
...and ALWAYS remember to Think Before You Click


