Defence-in-Depth
Defence-in-depth is a security discipline that refers to having layers of protection in an IT infrastructure. It is designed this way so that security is not dependent on any single layer, especially in the event of an attack. Organisations need to defend their networks on each of the seven areas in the diagram you see. End-user Security Awareness Training resides in the layer: ‘Policies, Procedures, and Awareness’. As you see, this is in reality is where security starts. You don’t open the door for the bad guy to come freely into your building, right? Let’s have a quick, and admittedly highly simplified, look at defence-in-depth.
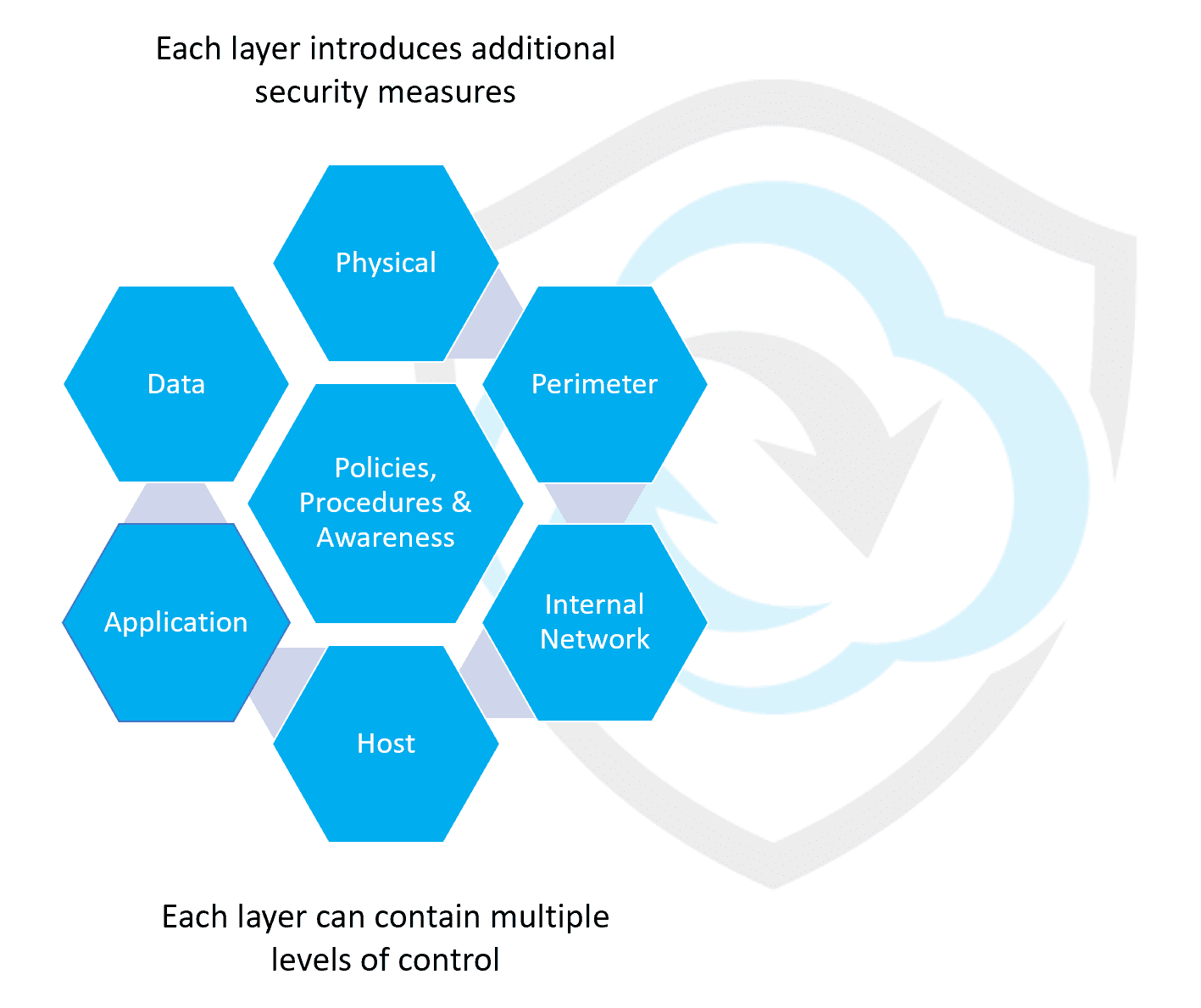
End-user Security Awareness is an important piece of your security puzzle because many attack types go after the end user (called social engineering) to succeed.
Once an organisation has published policies, has implemented security procedures, and has trained all employees, the first step of defence-in-depth has been established.
The second step is protecting your physical items. That usually means laptops, work stations, servers, mobile devices, etc. Can anyone walk into your server room?
The third step is defending the perimeter. In the case of IT that usually means a firewall, and related tools to block intrusions. With BYOD, your perimeter is expanded to each employee individually.
Part four is protection of the internal network. There are various software tools that scan the network for attackers, traffic that should not be there, and many other ways to detect attacks. These are the Intrusion Detection, Intrusion Prevention and Breach Detection kind of products.
Next, protecting each individual computer in the network (called ‘hosts’) is also crucial. Here is where end-point security tools like endpoint protection, firewalls, DNS protection and software whitelisting live, which attempt to block attacks on the individual computer level.
Then, there are many ways to protect the individual applications that are running on computers in the organisation, and last but not least, the data also needs to be protected, and yet again, there are many, many ways to do that, for example encryption. Practicing the Principle of Least Privilege will also mitigate the risk.
However, end-user security awareness can affect every aspect of an organisation’s security profile, as it truly is where security starts! That is why it is so important that Small and Medium Enterprises (including non-profits) give their end-users Internet Security Awareness Training, to educate and train their end users along with ensuring compliance.


