is a common tactic used by cyber criminals to manipulate people into sharing confidential information. Hackers exploit people’s trust, knowing that when we’re under pressure we may be more likely to make mistakes. The kind of information hackers seek out varies, but commonly includes bank account details, personal information and company files. Social engineering is a common tactic used by cyber criminals to manipulate people into sharing confidential information. Hackers exploit people’s trust, knowing that when we’re under pressure we may be more likely to make mistakes. The kind of information hackers seek out varies, but commonly includes bank account details, personal information and company files.
Hackers love to use social engineering because it’s easier to trick someone into sharing their password than to spend time trying to hack into an account. So, they lull victims into a false sense of security by gaining their trust and pretending to be someone else.
Social engineering attacks take many forms, but they commonly look like emails and messages from friends and trusted organisations:
Emails from Friends
Hackers spend a while collecting information about their targets, so if your social media followers and friends list are publicly visible it’s relatively easy for them to create fake email from a friend. These messages contain links, videos or images that include malware, so if you click on them they’ll gain instant access to your device and all your vital information.

Emails from Organisations
These kinds of cyberattack are known as phishing emails. Like fake friend emails, these can be very convincing and are designed to look like they’ve come from trusted sources, such as HMRC or your bank.
Once hackers have gained a target’s trust, they will create a sense of urgency by asking for help. This might be in the form of a desperate friend being stranded in a foreign country and needing some funds to be wired to them urgently, or a financial institution asking for you to verify personal information. They may also send a message claiming you’re the winner of an online competition, or pretending to be your boss or co-worker asking for client details.
The Cost of Social Engineering
The monetary cost of social engineering attacks on businesses vary according to different sources, from anywhere to £25,000 to upwards of £4 million.
The biggest social engineering attack recorded to date was led by Evaldas Rimasauskas, who successfully targeted Google and Facebook. He set up a fake company and bank account, posing as a computer manufacturer who worked with the two tech giants. His team of scammers then sent phishing emails to a number of employees within Facebook and Google, attaching invoices for work that had been genuinely undertaken by the real manufacturing company. The money was then deposited into fraudulent accounts, and over the course of two years over $100 million was extorted.
But perhaps the most important – and most often forgotten – impact of social engineering attacks is the human one. The guilt and shame associated with clicking on an infected email and causing huge organisational damage is too much for some people, with victims becoming depressed or developing severe anxiety. Two people are thought to have committed suicide following the Ashley Madison cyber-attack of 2015, and many others have lost their jobs and livelihoods.
How to Protect Yourself Against Social Engineering Attacks
Since social engineers like to act when people are more likely to be under pressure, it’s important to try to stay mindful and vigilant at all times. Here are some ways you can minimise the risk of a successful attack:
- Report and delete any messages that ask for financial information or passwords
- Set your spam filters to “high” and regularly check your folders to ensure no legitimate emails are in there
- Install robust anti-virus software, firewalls and email filters on all devices and user accounts
- Use multi-factor authentication and strong passwords, so even if anyone does manage to get hold of your password they’ll still be asked to provide further information if their credentials aren’t familiar
- Double check all email addresses claiming to be from friends or trusted sources before you respond – particularly if they contain links or ask for information
- Be wary of tempting offers – if it looks too good to be true, it probably is
- If in doubt, stop. Taking a few minutes to check whether something is legitimate is a lot less time consuming than clicking a link in haste
To find out more about how to keep your organisation safe, contact our friendly team of Cyber Security specialists at Actisoft Technology today.
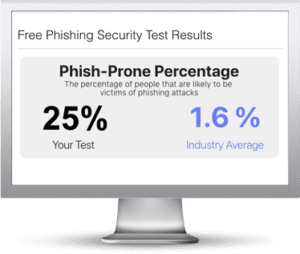
Start Your Free Phishing Security Test
Find out what percentage of your employees are Phish-prone
Did you know that 91% of successful data breaches started with a spear phishing attack?
Find out what percentage of your employees are Phish-prone™ with your free phishing security test. Plus, see how you stack up against your peers with the new phishing Industry Benchmarks!
IT pros have realised that simulated phishing tests are urgently needed as an additional security layer. Today, phishing your own users is just as important as having antivirus and a firewall. It is a fun and an effective cybersecurity best practice to patch your last line of defence: USERS
Why? If you don't do it yourself, the bad guys will.
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customise the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organisation compares to others in your industry
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Start phishing your users now. Fill out the form, and get started immediately!
