
Social engineering is the art of exploiting human psychology. Often referred to as “human hacking”, it’s a popular tool used by cyber criminals all over the world to gather valuable data and get unsuspecting victims to divulge confidential information, or hand over money.
But contrary to popular belief, social engineering isn’t just conducted by hackers surfing the dark web in dingy rooms. Everyone from main stream media to government bodies use human psychology to sway opinion and manipulate us into things we might not usually do, as evidenced by the Cambridge Analytica scandal of 2018. And the more time we spend online, the more opportunities we’re giving for our data to be used against us.
This might all sound like doom and gloom, but by applying our own knowledge and experience we can stay one step ahead of cyber criminals. And a great way to do that is to recognise ways in which we use social engineering in common business practices, like marketing.

A Brief History of Social Engineering
The term social engineering started to gain momentum in the 90’s, but the principle has been around for much longer. Fraudsters have been conning people for centuries, the first advance fee scam can be traced back to 1922. Dutch industrialist J.C. Van Marken first coined the phrase back in 1894 in reference to the practice of gaining information through deception, so this is far from a new concept. Technology just makes it easier.
In terms of cybersecurity, being aware of how criminals exploit people into giving up valuable data goes a long way towards online safety, and understanding how hackers try (and often succeed) to manipulate behaviour is crucial to risk management. Most of us know that cyber criminals use phishing attacks to get us to click on dodgy email links, but that doesn’t make us immune. What might seem like an obvious attack first thing on a Monday morning when we’re all bright eyed and alert might easily slip under the radar another time, when we’re overworked and stressed.
Cognitive Bias
Social engineering experts prey on the fact that the human mind is fallible. They know that we tend to make decisions based on shortcuts and clues we’ve learned in the past, so when we see something we instantly recognise, our brains tell us it’s ok. This quick decision making is known as “cognitive bias”, and although it’s an evolutionary tool that can come in very handy in day-to-day life, it can also get us into trouble. When we see a large black and white animal with four legs, hooves and udders, our past experiences automatically say “cow”. Most of the time, it probably is a cow (unless it’s a particularly large goat), but that logic doesn’t always serve us well.
The Psychology of Persuasion
Social engineering relies on six core principles of human behaviour, as outlined in Robert Cialdini’s book Influence: The Psychology of Persuasion :
- Reciprocity - do someone a favour and they’ll feel obliged to return it
- Commitment and consistency – people are more likely to honour an agreement if they’ve committed to it verbally or in writing
- Social proof- people tend to follow behaviours they’ve seen in other people, from vocalising popular opinions or wearing certain fashions
- Authority – people tend to follow orders and obey authority, even if they’re not comfortable with what they’re being asked to do
- Liking – if we like people, we tend to be more easily swayed by them
- Scarcity/Urgency – people naturally respond to situations when it looks like time is running out
These principles can be used in all sorts of ways, from getting someone to buy into a new product or service, to conning them into handing over all their money.
Social engineering has proven to be a great way for hackers to infiltrate organisations. They can gain someone’s password in a couple of seconds, and within an hour all that organisation’s confidential data could be gone. All it takes is a little bit of confidence and an understanding of the core principles outlined above.
The article Anatomy of a Hack describes how a penetration tester was able to use a combination of online information, a $4 uniform and a basic understanding of human nature to infiltrate an entire network… all in broad daylight. All he needed to do was act confident, be friendly and gain people’s trust, and the rest just fell into place.
It's Often a Slow Burn
Marketers know that a great result often takes weeks and months of preparation. If you want to run a successful social media marketing campaign or get your website at the top of Google searches, a huge amount of legwork and data collection has to go into it before the profits start rolling in. it’s the same with hacking. Criminals will often use a multi-pronged approach to get the information they need before making their attack, such as:
- Calling on the phone and pretending to be a trusted authority needing information about key personnel
- Attending the office and pretending to be an employee – it’s amazing how many people will hold the door open for strangers claiming to have misplaced their key cards
- Using pop culture, breaking news and high-profile competitions to lure people into clicking on links
- Researching employees on LinkedIn and Facebook and finding out their likes, dislikes and online behaviours, and customising phishing attacks based on that information
When justifying their behaviour, con artists will often say that greed is what lets their victims down. This was the foundation of Nigerian 419 scam that became a running joke over the years, where a prince needs help with transferring funds into a safe bank. Blinded by the offer of a cut of the money, victims willingly hand over their own bank details to the hacker, who’s never heard from again.
Although this scam reached its peak in the noughties, social engineers still use it to this day – and people still fall for it. As all good marketers know, everyone loves a freebie, so offering a sweet reward is a great way to catch people off guard.
Because most people tend to respect authority and follow rules, it’s relatively easy for hackers to dupe their victims simply by pretending to be someone important. In 2015 some highly trained, academically bright finance employees transferred millions of dollars of company money to scam artists posing as company executives. Just try a simple Google search and you’ll find lots of similar stories.
Tabloid journalists have even used this principle to access celebrities’ voicemails. In 2005, a private investigator working on behalf of The Sun was able to reset Sienna Miller’s voicemail password by calling Vodafone and claiming to be “John from credit control.” And in 2016, the head of Hillary Clinton’s presidential campaign had his email hacked by Russian spies by giving his login credentials to someone he believed to be a Google security expert.

Know Your Enemy
We are not for a minute suggesting that marketing is on a par with hacking in terms of morality. But we can draw parallels that will help us understand how hackers use similar tactics to manipulate and gather valuable information.
The concept of marketing is to influence others into making decisions, often preying on desire to fit in, fear of missing out and need to please. And just like we have a choice about whether to buy that shiny new gadget or pair of shoes, we also have a choice not to click on that link.
It’s important to remember that even the most complex hack is only as good as the people at the receiving end of it. If we don’t do what they want, they don’t get what they want. So, just taking a couple of seconds to breathe and check it out can prove invaluable.
Hackers are not mystical beings who think and behave like computers. They are normal people who look the same as everyone else and who use their experience and understanding of the human condition to make money. So, by understanding how we can manipulate human behaviour in our own work, we can be more attuned to how hackers’ brains work too.
To find out more about current hacking trends and how to keep your workforce one step ahead of the cyber criminals, get in touch. We offer a comprehensive range of product and services, including security awareness training for organisations of all sizes. Contact Us!
Free Phishing Security Test
Would your users fall for convincing phishing attacks? Take the first step now and find out before the bad guys do. Plus, see how you stack up against your peers with phishing Industry Benchmarks. The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
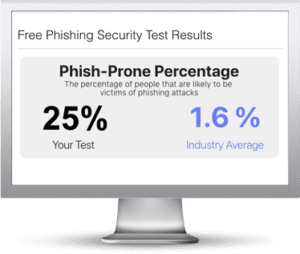
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customise the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organisation compares to others in your industry
