As the cyber threat landscape continues to evolve, passwords and anti-virus software simply aren’t enough anymore. And while there’s no silver bullet that totally eliminates all attacks, employing a Multi Layered Defence will definitely help.

What do we mean by Multi-Layered Defence?
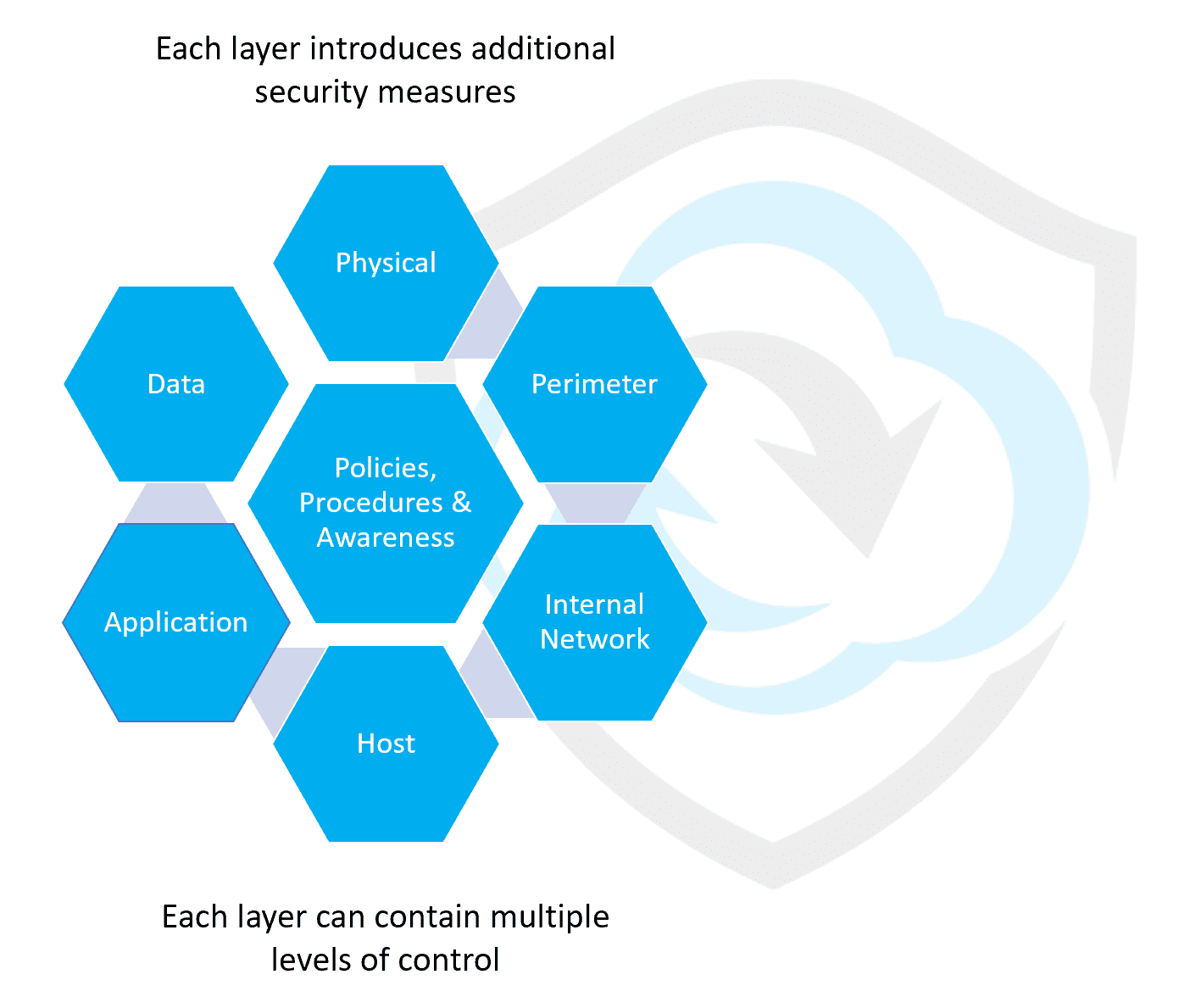
Also known as Defence-in-Depth and Layered Security, Multi-Layered Defence is an approach to network security that uses a variety of tools. The aim is to keep all bases covered by ensuring every individual aspect of your cyber security strategy has a backup to protect against vulnerabilities. Think of it in the same way as keeping your house secure – you can lock your doors and close your windows, but your home will be even safer if you’ve also got a burglar alarm and security cameras installed. When you’ve got an arsenal of protection working together against hackers and other threats, your business will be more secure too.
Multi-Layered Defence is recognised as Best Practice, as recommended by the National Institute of Standards and Technology (NIST) Cyber Security Framework. The framework outlines five key areas to help businesses protect their systems and data:
- Identify
- Protect
- Detect
- Respond
- Recover

Networks can be defended by implementing twelve essential layers, as outlined below.
1) Firewalls: A firewall is commonly the first line of defence in an organisation’s network security, acting as a barrier between the network and any unsolicited traffic.
2) Patch Management: Hackers are always on the lookout for vulnerabilities, and outdated software often provides them with the perfect way in. Patch management is essential because it means errors and bugs can be easily identified and fixed, making it far harder for cyber criminals to strike.
3) Multi-Factor Authentication: An MFA is an electronic automation method that requires users to be verified in two or more ways before they’re granted access to particular networks, applications and websites. Users are asked to provide information on:
- Something they know (e.g., a password or PIN)
- Something they have (a physical object, like a card, security key or mobile device)
- Something they are (this method uses biometric verification, such as fingerprints, voice recognition and retina scans). While it may sound like a lot to ask a user, these solutions have been developed so effectively and efficiently that they’re easy to use and cause minimal disruption.
4) Endpoint Protection: Today’s businesses have a lot of different devices logging onto their networks, which significantly increases security risks. Every phone, laptop, PC , camera, printer, scanner and smart device (known as “endpoints”) must be individually protected as part of your cyber security strategy.
5) Content Filtering: There’s an enormous amount of web content out there, and if just one of your users happens to access a dangerous website your entire network could be compromised. Web content filtering allows you to block inappropriate or untrusted sources that could put you at risk of cyber-attacks.
6) Email Filtering: The vast majority of cyber-attacks - 94% to be precise - are still delivered by email. Hackers know all it takes is one click on a dodgy link for an entire network to be compromised, so by filtering emails before they arrive in users’ inboxes you can help stop them in their tracks.
7) Security Awareness Training: Knowledge is power, so many experts believe that educating employees is often the best line of defence. By providing staff with the training they need to spot common hacking tactics, such as phishing emails, you will be creating a culture of security and confidence. Threats evolve rapidly, so it’s important to keep training up to date and relevant, and it’s a good idea to conduct regular phishing simulations to keep people on the ball.
8) Robust Password Policies: A recent study from NordPass revealed that millions of people still use “qwerty” and “123246” as their passwords, and – even more concerning - over half of IT professionals still use the same password to access different accounts. In fact, as many as 73% of passwords are duplicates, which means if one account is hacked, the chances are your others will be too. By requiring users to change to complex passwords (containing special characters, numbers and inconsistent capitalisation) you’ll be making it much harder for hackers to break in.
9) Physical Barriers: Although much of modern business is conducted online, it’s still important to consider what physical security you’re using in your workplace. Security staff, cameras, alarms, key cards and good old-fashioned locks are still as effective as the ever were, and combined with modern biometric tools like thumb and retina scans they go a long way towards preventing crime.
10) Dark Web Monitoring: The dark web is notoriously a hotbed of illicit, insidious online activities, which includes the sale of business-critical data. Employee data is often targeted, enabling hackers to send malicious emails and install viruses. You can invest in tools that search the dark web for staff email addresses and passwords to keep you one step ahead.
11) Disaster Recovery: With new threats emerging all the time and the security landscape becoming increasingly complex, it’s impossible for anyone to offer 100% certainty against attacks. But what you can do is ensure that if the worst does happen, you’ve got the right business continuity and disaster recovery methods in place. These solutions include performing regular data backups and making sure your business continuity plan is routinely tested, maintained and updated, vastly improving your chances of getting back to business quickly and with minimal disruption.
12) Managed Detection and Response: It’s impossible for one human (or even a whole team of them) to monitor a system 24/7 and detect potential threats. Managed Detection and Response (MDR) is a solution that combines human skill and experience with state-of-the-art software to ensure your network is as safe as possible, all day, every day. Without the right tools data breaches can go unnoticed for over 200 days, which means cyber criminals to wreak havoc while you’re blissfully unaware.
If you want to do more to protect your organisation’s data and reputation, contact us today to find out more about our Multi-Layered Defence services.
Find out now how many of your users take the bait and reply to a spoofed email
Did you know that 60% of spoofed email attacks do not include a malicious link or attachment? When crafted well, most users are likely to fall victim to a highly targeted social engineering attack.
Try our Phishing Reply Test (PRT) it is a complimentary IT security tool that makes it easy for you to check to see if key users in your organisation will reply to a highly targeted impersonation attack.
PRT will give you quick insights into how many users will take the bait so you can take action to train your users and better protect your organisation from these fraudulent attacks!
Here's how it works:
- Immediately start your test with your choice of three phishing reply scenarios
- Spoof a Sender's name and email address your users know and trust
- Phishes for user replies and returns the results to you within minutes
- Get a PDF emailed to you within 24 hours with the percentage of users that replied
Identify how many users take the bait and reply before the bad guys do!