Blog courtesy of KnowBe4
Written by Stu Sjouwerman
New data shows that pushback from the ransomware victim “market” may be influencing just how much cybercriminals are asking for as ransom and are being paid.
2020 seemed to point to ransomware continuing to grow in devastation and cost; Ryuk reached a $34 million ransom payout, organisations were operationally brought to their knees by many of the prominent ransomware families, and the “as-a-Service” market for various parts of ransomware attacks – including the publishing of exfiltrated data – grew in interest.
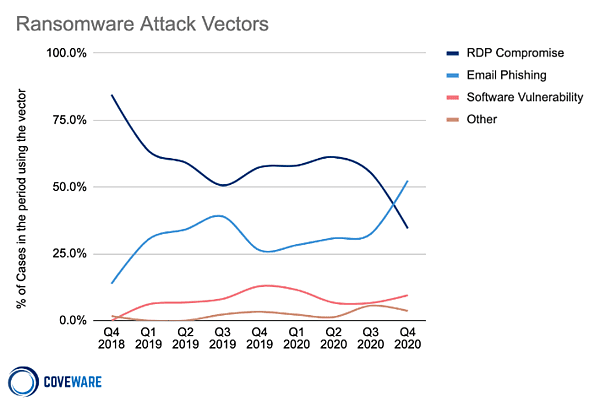
But new data from security vendor Coveware in their Q4 2020 Quarterly Ransomware Report shows that phishing is now the prominent ransomware attack vector since RDP compromise is being prevented by potential victims.
There are also some shifts in payment amounts – fortunately in the favour of the victim organisations.
According to the report:
- The average ransom payment decreased 34% in Q4 of 2020 to $154,108 from $233,817 in Q3
- The median payment also decreased by 55% in the same timeframe from $110,532 to $49,450
- Threats to disclose exfiltrated data stepped up in Q4, with a whopping 70% of ransomware attacks using this tactic (up from 50% in Q3)
Coveware speculate this decline in payment amounts is due to the ability for organisations to better recover their locked environment. And with Coveware seeing that exfiltrated data doesn’t appear to be credibly destroyed by the cybercriminal (and instead appear to be found in the hands of multiple parties, implying it’s been sold on the dark web), there is less emphasis on the option to pay the ransom and stop the publishing of the stolen data.
Phishing took over from RDP as the top overall initial attack vector, with the top attack vector varying between ransomware families. RDP picked up steam during the pandemic as many organisations sought to quickly provide remote access to their now remote workforce. Phishing has moved up as the quickest route to get malicious code into an organisation and in front of an unwitting victim user.
If you haven’t heard it yet: stop using Internet-facing RDP. Changing the ports isn’t enough; it’s time to pick another more secure technology. And for phishing, many ransomware attacks continue to make it through your email filters. You need to block attacks that have made it in your users' inbox. Turn your users into a strong human firewall with new-school security awareness training and enable your users to make smart security decisions every day.
Ransomware Has Gone Nuclear, How Can You Avoid Becoming The Next Victim?
There is a reason more than half of today’s ransomware victims end up paying the ransom. Cyber-criminals have become thoughtful; taking time to maximise your organisation’s potential damage and their payoff.
After achieving root access, the bad guys explore your network reading email, finding data troves and once they know you, they craft a plan to cause the most panic, pain, and operational disruption. Ransomware has gone nuclear.

Join us for this webinar where, Roger Grimes, KnowBe4’s Data-Driven Defense Evangelist, dives into:
- Why data backups (even offline backups) won’t save you
- Evolved threats from data-theft, credential leaks, and corporate impersonation
- Why ransomware isn’t your real problem
- How your end users can become your best, last line of defence