Ransomware
Ransomware is a devastating type of Malware with global damage projected to cost organisations $265 billion by 2031. Get the Information you need to prevent infections, and find out what to do if you are hit
What is Ransomware?
Ransomware is defined as vicious malware that locks users out of their devices or blocks access to files until a sum of money or ransom is paid. Ransomware attacks cause downtime, data loss, possible intellectual property theft, and in certain industries an attack is considered a data breach.
September 2013 is when ransomware went pro. It typically gets installed on a user’s workstation (PC or Mac) using a social engineering attack where the user gets tricked into clicking on a phishing link or opening an attachment. Other attack vectors include unpatched programs, password guessing, compromised vendors, poisoned online advertising and free software downloads. Once the malware is on the machine, it starts to encrypt all data files it can find on the machine itself and on any network shares the PC has access to. This can lead to catastrophic situations in which a single computer can halt an entire organisation or department.
When a user wants to access one of these files they are blocked, and the system admin who gets alerted by the user finds two files in the directory that indicate the files are taken ransom, and how to pay the ransom to decrypt the files. New strains and variants come and go as new cyber mafias muscle into the "business". Techniques the cyber criminals are using are constantly evolving to get past traditional defences. Some major strains are Ryuk, Dharma, Bitpaymer and SamSam. This is a very successful criminal business model. Annual ransomware-induced costs are projected to exceed $20 billion by 2021, according to a Cyber Security Ventures report.
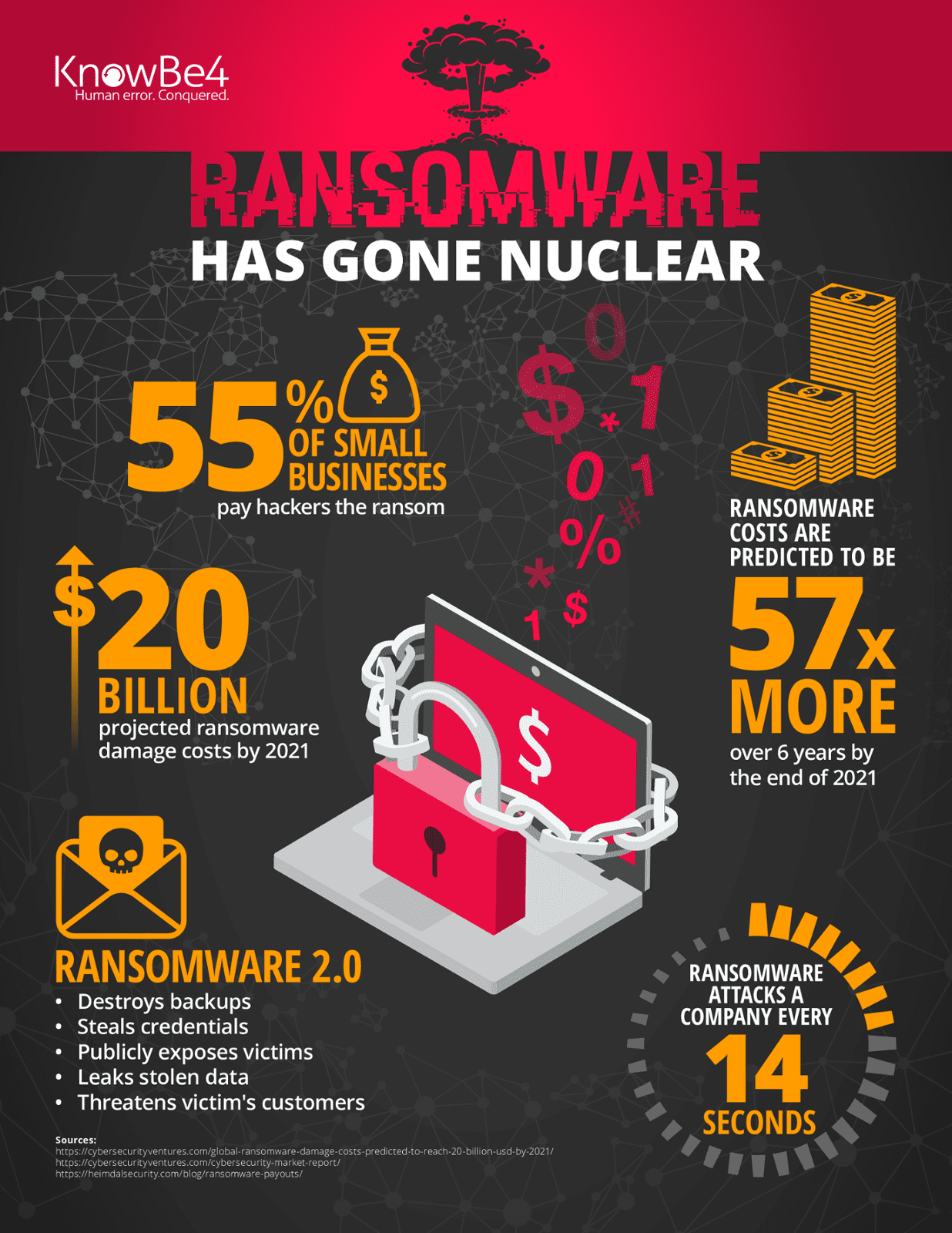
Once files are encrypted, the only way to get them back is to restore a backup or pay the ransom. However, cyber criminals are now often corrupting backups before the victims know what hit them. Storage Magazine reports that over 34% of companies do not test their backups and of those tested 77% found that tape backups failed to restore. According to Microsoft, 42% of attempted recoveries from tape backups in the past year have failed.
In 2020, a Ransomware Infection is a Data Breach
The emergence of new strains has slowed down, but ransomware has gone nuclear and is getting much more sophisticated. In the early days, hackers mostly targeted consumers, and it would encrypt immediately upon executing. Later on, ransomware gangs realised they would make a lot more money targeting businesses. At first they would spread like a worm through organisations, collecting credentials and encrypting files along the way. Threat actors are now a lot more intelligent in their approach. Once they've gotten in, the malware 'dials home' so that the hacker can do a full analysis on which data is most valuable to their victim, how much they can realistically ask for, and what can they encrypt that will get them a payday sooner.
Most of the ransomware gangs are now exfiltrating your most valuable data and threaten to expose it on publicly available websites as an additional extortion method. Some of these criminals make you pay twice, once for the decryption key, and again to delete the data they have stolen. In the U.S. alone, a single cyber security insurance consortium said they are paying $1M per day in ransomware payouts to these criminal gangs.
That figure doesn't include recovery and downtime costs, which can far exceed the cost of the ransom. By now, there are tens of thousands of ransomware victims, including school districts, police departments, and entire cities. It is important to understand that it is not just large organisations that are targeted, small and medium organisations are also at risk.
Cyber criminals constantly use social engineering and update their ransomware themes to stay current. Some themes include the FBI variant, the Internal Revenue Service, and even sadly, now COVID-19 pandemic-themed ransomware. In addition to updating themes, cyber criminals are also developing creative new ways to spread the ransomware. These include offering Ransomware-as-a-Service (RaaS) strains such as “Dot” or “Philadelphia”, where they offer your files back for free if you infect two other organisations. There are even marketing videos on YouTube for some ransomware strains.
Is your network effective in blocking ransomware attacks?
Bad guys are constantly coming out with new strains to evade detection. Is your network effective in blocking all of them when employees fall for social engineering attacks?
KnowBe4’s RanSim gives you a quick look at the effectiveness of your existing network protection. RanSim simulates 15 ransomware infection scenarios and 1 cryptomining scenario and will show you if your workstation is vulnerable.
5 Ways to Prevent a Ransomware Attack in 2020
It’s a given that ransomware is here to stay for the foreseeable future. It’s not new, so organisations should be pretty well-versed in how to stave an attack, as well as how to remediate one should it successfully encrypt the organisation’s data and/or systems. However, ransomware claims are up 50% in 2019 with attacks outpacing the previous five years. This is indicative that organisations are largely unprepared for an attack. The best time to get serious about prevention is before an attack, not after. Shawn Taylor at Dark Reading lays out 5 excellent cyber security resolutions to consider in 2020:
- Basic Cyber Security Hygiene. Improving basic cyber security hygiene is the No. 1 defence against any type of attack, including ransomware. This is the cyber security version of many people's New Year's resolution to "get healthy." Cyber Security hygiene can mean a lot of different things, but a good place for companies to start is by making sure they have strong vulnerability management practices in place and that their devices have the latest security patches. They can also make sure they are taking basic security precautions that are often also important for regulatory compliance, like running up-to-date antivirus software or restricting access to systems that can't be made compliant. Ultimately, however, for most organisations, starting with CIS Control 1, Inventory and Control of Hardware Assets, will establish a good foundation upon which to build.
- Penetration Testing. Companies that already have much of the basic hygiene in place can take the additional step of engaging pen testers to further ensure that anything Internet-facing in their organisation is protected. By finding what means or mechanisms attackers could hack or brute-force an attack to gain access to applications or internal systems by bypassing other protections such as firewalls, security leaders can fix those areas before bad actors find them.
- Board Discussions. Cyber security is increasingly becoming a board of directors-level issue. That's because an attack can have a significant impact on a company's revenue, brand, reputation, and ongoing operations. However, it's worth having a specific board-level conversation about ransomware to ensure they understand the specific risks it could pose to the business, and that there is budget made available to prevent or limit the damage of an attack. That discussion will prove critical if the company wants to implement added protections, such as improved cyber hygiene, or put in place automated reactive technologies to limit the spread of an attack. If the CIO or CISO is not already regularly having these conversations about cyber security or ransomware in particular, that's definitely a good place to start for 2020.
- Tailored Training. There is one vulnerability that has proven effective again and again as an entry point for attack: people. You can buy all the latest and greatest cybe rsecurity technology, but if you aren't training your employees in basic cyber security or how to respond during an attack, then you're leaving yourself vulnerable. Training to prevent ransomware starts by teaching employees to recognise phishing attacks and what to do if they suspect one. This is important because — even though many users have gotten better — phishing remains one of the most effective ways for an attacker to breach an organisation. Teaching users to validate URLs or avoid clicking on links or attachments altogether can go a long way toward protecting against all types of attacks. This is a good practice to start or revisit in 2020.
In addition to preventing an attack, security leaders can also think about adding specific training for ransomware response. It's pretty easy for an employee to know when they've been hit with ransomware — their work screen may go away and they may get a pop-up directing you to a URL to pay the ransomware (likely in bitcoin). Training employees in what steps they can take in response or giving them an emergency point of contact on the security team can make them feel more in control in the panic of an attack. - In addition to preventing an attack, security leaders can also think about adding specific training for ransomware response. It's pretty easy for an employee to know when they've been hit with ransomware — their work screen may go away and they may get a pop-up directing you to a URL to pay the ransomware (likely in bitcoin). Training employees in what steps they can take in response or giving them an emergency point of contact on the security team can make them feel more in control in the panic of an attack.
- Limit the Scope of an Attack. Ransomware resolutions should include not only preventing an attack but also taking steps to minimise the damage of a successful one. That starts with having tools in place, such as SIEM (Security Incident and Event Management) systems that can identify the behaviour patterns and heuristics of an attack and begin to automatically isolate and remediate those systems when indicators are flagged. It also means embracing tools such as network segmentation that can prevent the lateral movement of an attack across the network


