Phishing is an attempt by cybercriminals posing as legitimate institutions, usually (but not always!) via email, to obtain sensitive information from targeted individuals.
These attacks are on the rise, with more than 80% of organisations being targeted in 2021 alone. One of the most frustrating things about phishing is that these attacks are becoming so realistic and sophisticated that it’s becoming increasingly hard to spot them. So, even if you think you know everything there is to know about online scams, it’s still surprisingly easy to get caught out.
There are many different types of phishing, but in this post we’ll concentrate on the most common types affecting UK businesses right now.

Email Phishing
Most phishing attacks are deployed via email, and hackers are getting really good at creating fake accounts that look just like the real thing. They register fake domains that mimic well known organisations (such as Amazon, the NHS or Google) and send thousands of generic emails in what’s known as a “spray and pray” approach. The idea is that if they send a massive amount of emails, at least a few people will respond.
These attacks are on the rise because they work. The fake domains they create are so realistic that targets have to look really closely – they copy the logos and font type exactly, and often just one character is out of place in the email address. Many recipients see something that looks very familiar and assume it’s safe. As soon as they click on the link or download the attachment, it’s too late.

Spear Phishing
This is a more sophisticated type of email phishing attack. Instead of using a “spray and pray” approach cyber criminals will target particular people within an organisation, which involves more time and effort.
Before they send their malicious emails, hackers will have gathered important information about their targets including things like their name, job title, work location, email address and other specific information about their role. These attacks are particularly hard to identify because they address the user by name and often refer to other members of staff, meetings or work activities that are familiar to the target. Unlike the email scams of old, they’re often written in perfect English and seem totally legitimate – so it’s often only a matter of time before the hacker has access to the user’s data.
Whaling
Whaling attacks go a step further, and are usually aimed at senior staff members within an organisation. Whaling emails tend to be more subtle, and they’re less likely to use tricks like fake links. Instead, they’re likely to pose as a CEO or board member requesting vital information or the transfer of funds. The hackers create a sense of urgency, saying things like “I know you might be busy but really need you to get this done now” and they rely on employees being keen to keep their bosses happy.
Angler Phishing
This is a relatively new form of attack, which is deployed via social media. Hackers share posts including fake URLs, cloned websites and infected links and use instant messages to encourage victims to download malware. Cyber criminals keep an eye out for customers contacting organisations with complaints, then hijack the organisations’ social media accounts and ask for the customers to provide their bank account details in order to receive a refund. Of course, that refund never happens, and scammers walk away with valuable data and banking information.
Smishing and Vishing
These are more like old school hacks because they take place over the phone rather than via email, but they’re no less damaging. In a smishing attack, the victim will receive a text message asking them to follow a link or download a piece of software to their phones, while a vishing attack involves a telephone conversation. A common tactic is for criminals to pretend to be calling from a bank, alerting victims to suspicious activities on their accounts. Attacks of this kind can look incredibly realistic these days, and hackers rely on the fact that when people are stressed and under pressure they’re more likely to make silly mistakes.
Phishing attacks are estimated to cost the UK economy over £5 billion a year. The best way to prevent these attacks is with anti-phishing and anti-spam software, but it’s also essential to stay aware and on guard – which goes for smishing and vishing too. This means ensuring all staff are regularly trained and understand how to spot a potential threat.
For more detail about different types of phishing, our partner Fortinet has put together a comprehensive list you can also visit our Phishing page. We are also happy to talk to you about the most common threats to your organisation and deliver cyber security training. Contact us today for a no obligation quote!
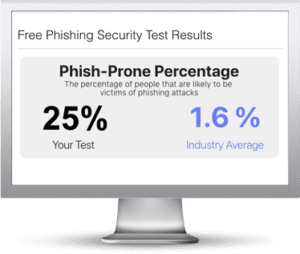
Start Your Free Phishing Security Test
Find out what percentage of your employees are Phish-prone
Did you know that 91% of successful data breaches started with a spear phishing attack?
Find out what percentage of your employees are Phish-prone™ with your free phishing security test. Plus, see how you stack up against your peers with the new phishing Industry Benchmarks!
IT pros have realised that simulated phishing tests are urgently needed as an additional security layer. Today, phishing your own users is just as important as having antivirus and a firewall. It is a fun and an effective cybersecurity best practice to patch your last line of defence: USERS
Why? If you don't do it yourself, the bad guys will.
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customise the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organisation compares to others in your industry
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Start phishing your users now. Fill out the form, and get started immediately!
