If you’re running a small to medium sized business, it’s easy to think that you might not be a big enough fish to attract the interest of cyber criminals. But the truth is, small organisations are just as much at risk of hacks and other security threats as huge corporations – in fact, being smaller may make you more of a target.
Attackers are targeting thousands of businesses every day, and those with less robust defences in place make much easier prey than bigger organisations who can invest more time and money into cyber security.
Hackers also love targeting small businesses because they often deal with large sums of money and have great contacts – which means there’s lots of lovely data to steal.
It's often said that knowledge is power, and that’s certainly true when it comes to cyber-crime. The owners and managers of SMEs need to be aware of the risks, which is why we’ve put together this short article outlining the most common cyber-attacks right now and what we have seen.

1) Phishing
By far the most prevalent – and damaging – threat facing small and medium sized businesses in 2022 is phishing. These attacks account for 90% of all breaches; a figure that’s grown by 65% since 2021. Phishing attacks are when a hacker sends an email pretending to be from trusted contact, tricking the recipient to click on a malicious link, download a code or share sensitive information. There are several types of phishing attacks you need to know about:
- The spray and pray approach, which is where hackers send out thousands of emails all at once, in the hope that one or two will bite
- Spear phishing: a campaign that targets a particular person or organisation and includes information which is known to be of interest to the specific target
- Whaling: an even more targeted and carefully executed attack, where the hacker goes after a specific C level executive in the organisation
Phishing attacks are becoming increasingly sophisticated, which means that even if you think you’ve seen it all before, you could still be caught out.
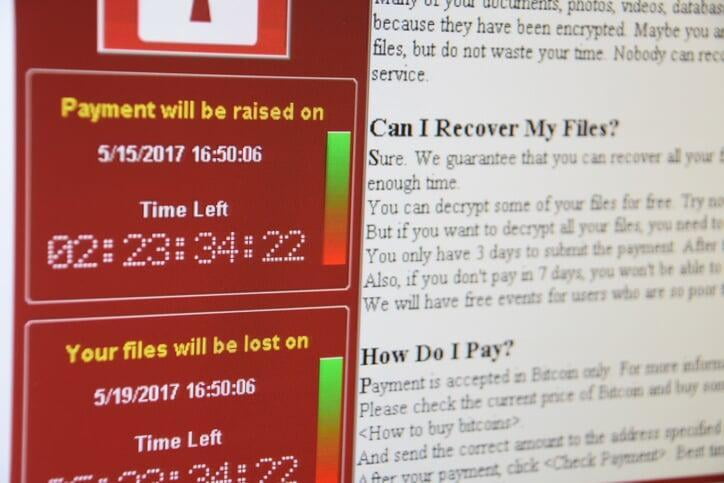
2) Ransomware
Ransomware is a type of malicious software which prevents or restricts users from accessing their computer systems and data, commonly by locking their screens and/or files until they pay a ransom. Like other cyber-attacks, ransomware technology has become more sophisticated over recent years. A popular attack at the moment is a breed of ransomware known as “cryptoransomware” where files are encrypted and users are forced to send an online payment in return for a decryption code.
Hackers will push for payments in all sorts of ways, though. The costs vary according to the type of ransomware being used and different exchange rates. Users are often asked to pay their ransoms in bitcoin, because it offers a greater level of anonymity, but hackers also list alternative options such as Amazon gift cards or iTunes vouchers. Sometimes it seems like an easy option to just pay up, but it should be noted that paying the ransom is no guarantee your files will be returned.

3) Social Engineering
Social engineering plays a huge role in cyber-crime. Even though advances in technology have been behind more sophisticated attacks, those attacks can only be properly deployed by a human. So, hackers work hard to understand how people think and manipulate them into making security mistakes or sharing valuable data. Social engineering happens in several phases. First, the hacker investigates their victim and identifies any weaknesses in their security systems. Next they start to gain their trust, either by sharing information the victim might be interested in or by pretending to be a trusted contact. Then, when the target lets their guard down and begins to trust the hacker, they’ll go in for the kill.
4) Insider Threat
Insider threats are posed by individuals from inside an organisation. This can include current or previous staff members, partners and contractors with access to passwords and company data. These individuals may act maliciously, intentionally stealing data or infiltrating systems for personal gain, but often they’re completely unwitting. Lack of awareness about cyber security issues can turn the most diligent worker into an insider threat, so it’s important to have robust policies and training measures in place.

5) Shadow IT
Shadow IT is a term covering the use of different IT systems, apps, services and devices that haven’t been approved by an IT department. Since Cloud services have become more popular, and also since the first lockdown, the use of Shadow IT has grown exponentially. New technology drives innovation and can deliver huge cost and time savings, but without the right security measures in place it also poses a huge risk.

6) Software Exploits
A software exploit is a code that’s been written to take advantage of a particular vulnerability or flaw in a piece of software. Although security professionals sometimes develop these exploits as evidence of vulnerabilities, they’re also widely used by hackers with malicious intent.
The purpose of this article is to provide you with an overview of the most common threats to your organisation. We’ll go into more detail about each type (and a few others!) in our next articles. In the meantime, if you want to know more about how to protect your SME from cyber threats, get in touch!
Are your users putting a big target on your organisation’s back?
Cybercriminals are constantly coming out with new ways to hack into your network and steal your organisation’s confidential information.
Find out if your users are putting a big target on your organisation’s back.
KnowBe4’s new Password Exposure Test (PET) is a complimentary IT security tool that allows you to run an in-depth analysis of your organisation’s hidden exposure risk associated with your users.
PET makes it easy for you to identify users with exposed emails publicly available on the web, and checks your Active Directory to see if they are using weak or compromised passwords that are part of a known data breach. PET then reports on any user accounts affected so you can take action immediately!
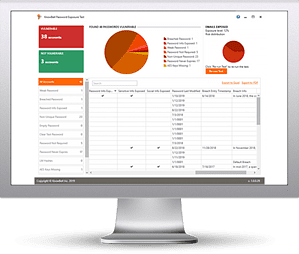
Here's how it works:
- Checks to see if any of your organisations email addresses have been part of a data breach
- Tests against 10 types of weak password related threats associated with user accounts
- Checks against breached or weak passwords currently in use in your Active Directory
- Reports on the accounts affected and does not show/report on actual passwords
- Just download the install, run it, get results in minutes!
Identify how many users take the bait and reply before the bad guys do!
