Insider threats represent a huge security risk to all organisations, and research suggests that the average cost is almost twice that of other types of breach. Whether the people behind the threats are acting nefariously or are completely oblivious to what they’ve done, the impact is just as serious. While business leaders are becoming more aware of the risk of insider threats, many organisations still lack the resources and knowledge to protect their data. In this article, we’ll take a look at the different types of insider threat, discuss the associated costs and show you how to mitigate risk.
What is an Insider Threat?
The term “Insider Threat” is used in the cyber security industry to describe any kind of threat posed by individuals from within an organisation. This can include current employees, stakeholders, contractors, board members, partners and previous employees. Basically, it refers to anyone who has the potential to access networks and put them at risk, whether intentionally or accidentally. The kind of information at risk of being compromised might be financial records, customer and employee data, passwords, business contracts or details of the organisation’s security procedures.
Insider Threats fall into two broad categories: intentional and unintentional. .

Intentional Threats tend to come from disgruntled employees, current staff members or contractors who misuse systems for their own personal gain and/or to cause disruption. People may work alone or in partnership with others, such as hacking organisations or business competitors.
Unintentional Threats are down to user error and lack of awareness. Those without adequate training and knowledge about cyber security issues can inadvertently put their networks at risk by falling prey to phishing scams, exercising poor password security or sharing data on compromised devices.
Different Types of Insider Threats
There are several different types of insider threat:
Second Streamers
This refers to current employees who intentionally misuse their organisation’s confidential data, either for financial gain or while working in partnership with others. Second streamers are thought to account for about 62% of all insider threats.
Angry Ex-Employees
When people feel wronged, they sometimes want to seek revenge – and compromising valuable data is a great way to do it. About 29% of disgruntled ex-employees committing deliberate sabotage do so for personal financial gain, while others act purely maliciously and want to cause as much damage and disruption as possible.
Inadvertent Insiders
This is one of the most common types of insider threat facing organisations today, and it’s all down to user error. People often don’t realise they’ve made a mistake (such as clicking on a dodgy link or sharing financial records with a convincing fraudster) until it’s too late, which is why it’s essential for all employees to have robust, regular cyber security awareness training.
Persistent Non-Responder
If you regularly hear someone say something like “all these security measures are just a waste of time, who would want to attack us anyway?” you’re probably dealing with a persistent non responder. Anyone who consistently refuses to adopt appropriate security protocols and continues to share passwords or use insecure devices is a risk – and it’s not always who you might expect. CEOs and board members are often the worst offenders.
How to Mitigate Risk
The cyber security landscape is constantly evolving and notoriously complex, so it’s impossible to completely eliminate risk. However, by adopting a multi-layered approach and ensuring you’re completely transparent about what you expect of your employees, it’s entirely possible to significantly reduce the risk of insider threats. Here are just a few measures you can take to protect your organisation:
- Undertake regular risk assessments to assess the likelihood of an attack
- Ensure all staff have regular security awareness training
- Maintain close management of all user permissions and ensure that leavers are immediately removed from your systems
- Undertake penetration testing at least once a year
- Implement 24/7 network monitoring
- Organise a cyber security assessment/simulated phishing attack
- Set up a managed detection and response system
Minimising the risk of insider threats doesn’t have to be hard work when you have the right team on your side. Contact our friendly specialists at Actisoft today to find out how we can help.
Start Your Free Phishing Security Test
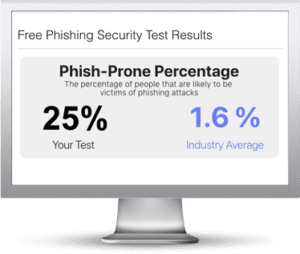
Find out what percentage of your employees are Phish-prone
Did you know that 91% of successful data breaches started with a spear phishing attack?
Find out what percentage of your employees are Phish-prone™ with your free phishing security test. Plus, see how you stack up against your peers with the new phishing Industry Benchmarks!
IT pros have realised that simulated phishing tests are urgently needed as an additional security layer. Today, phishing your own users is just as important as having antivirus and a firewall. It is a fun and an effective cybersecurity best practice to patch your last line of defence: USERS
Why? If you don't do it yourself, the bad guys will.
Here's how it works:
- Immediately start your test for up to 100 users (no need to talk to anyone)
- Select from 20+ languages and customise the phishing test template based on your environment
- Choose the landing page your users see after they click
- Show users which red flags they missed, or a 404 page
- Get a PDF emailed to you in 24 hours with your Phish-prone % and charts to share with management
- See how your organisation compares to others in your industry
The Phish-prone percentage is usually higher than you expect and is great ammo to get budget.
Start phishing your users now. Fill out the form, and get started immediately!
